You don’t have to deal with public IP, DDNS, SSL certificates or opening ports on your router.
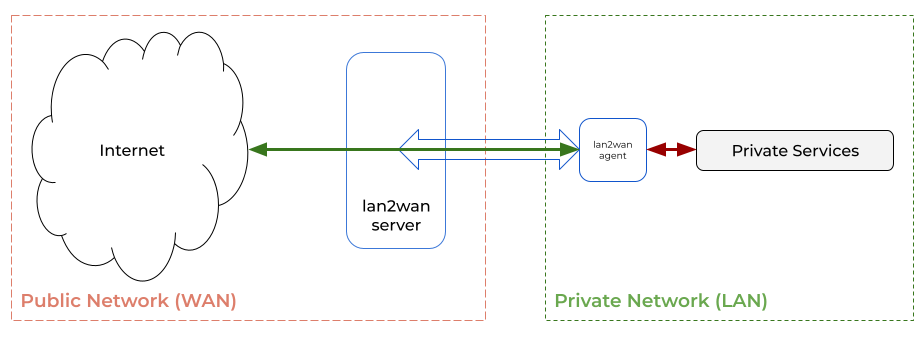
lan2wan service allows you to access your local services from the internet.
You can publish your service in a single command.
Example: publishing my local web application to the internet
$ lan2wan publish http://localhost:8080 --username hello --password my_secret
Local URL http://localhost:8080
Remote URL / HTTP http://xzmjg-106-220-244-187.free-tier.in-blr1.lan2wan.online
Remote URL / HTTPS https://xzmjg-106-220-244-187.free-tier.in-blr1.lan2wan.online
Encrypted tunnel
When you publish your services, lan2wan agent creates an encrypted tunnel over the entire communication.Features
- Supports end-to-end encryption
- You will get a random domain name, or you can use your custom domain
- You can add additional authentications in front of your local services.
- You can manage your endpoint settings via lan2wan console
Supported endpoints
- http
- https
- file browser
- tcp (via websocket)
HTTPS Certificate Management
When you publish your local services, You should add certificates to allow your connection is secure and encrypted. Here are the options available to manage your certificates.
Note
All the time lan2wan agent and lan2wan server communication will be encrypted.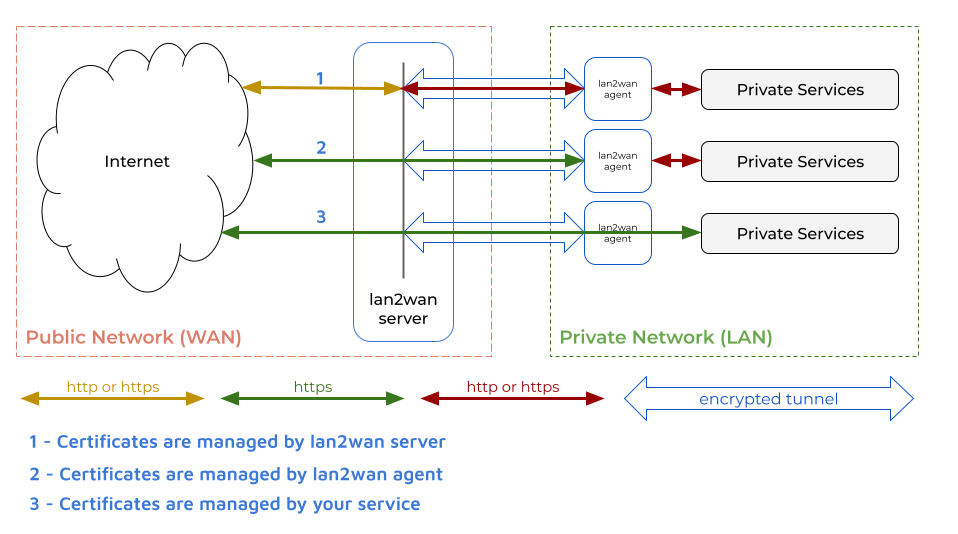
- Managed by lan2wan server
1 - Managed by lan2wan Agent (aka end-to-end encryption)
2 - Managed by your service (aka end-to-end encryption)
3
1. Managed by lan2wan server
In this mode certificate will be managed by lan2wan server.
Note
In this mode for user defined domains and native custom domains, Self-Signed certificate will be used.Letsencrypt certificates will be used only for the random domain generated at runtime.
2. Managed by lan2wan Agent (aka end-to-end encryption)
Also called as end-to-end encryption. In this mode certificate will be managed by lan2wan agent.
You can also provide your own certificate or lan2wan agent can get certificate from letsencrypt by default.
There is an option to specify your own ACME.
Downloaded certificates will be stored under ./certs directory in the agent location.
In addition to manage certificate also manages renewals automatically.
3. Managed by your service (aka end-to-end encryption)
Also called as end-to-end encryption. In this mode you service has to manage the certificates
Authentication Providers Not Supported
In this mode you can not use additional authentication feature.end-to-end encryption
Encrypts entire communication between your browser to your local instance.You can validate that there is no man-in-the-middle attack(MITM) happening by making sure that the certificate fingerprints matches with the local service certificate fingerprint.